In todays attacks especially when were talking about drive-by-downloads leveraging the iFrame tag is often the preferred method blogged researcher Peter Gramantik. This must be done to ensure that the.

Frame Injection Attacks Netsparker
When clicked this HTML element will disappear and be logged as a conversion.
. And listen to it in the iframe. Initially use an opacity of 01 so that you can align the iframe actions and adjust the position values as necessary. This attack is typically used in conjunction with some form of social engineering as the attack is exploiting a code-based vulnerability and a users trust.
Its simple and easy and with a few attribute modifications the attacker is able to embed code from another site often compromised and load something via the client. They are the element names surrounded by angle brackets and are of two types the start tag also known as opening tag and the end tag referred to as the closing oneBrowsers do not display these HTML tags but utilize them to grab up the content of the. Installation of XSS-Loader Tool on Kali Linux OS.
The frame enables a developer to split the screen horizontally or vertically by using the frameset tag. For the submitted attack a value of 00001 will work. This type of attack redirects visitors to a malicious site which will then install a virus to the visitors PC or attempt to steal sensitive information.
To track iFrame conversions follow these steps. The tag defines a rectangular region within the document in which the browser can display a separate document including scrollbars and borders. The solution provided in this article allows you to track the intent to convert by adding a clickable HTML element surrounding the iFrame element.
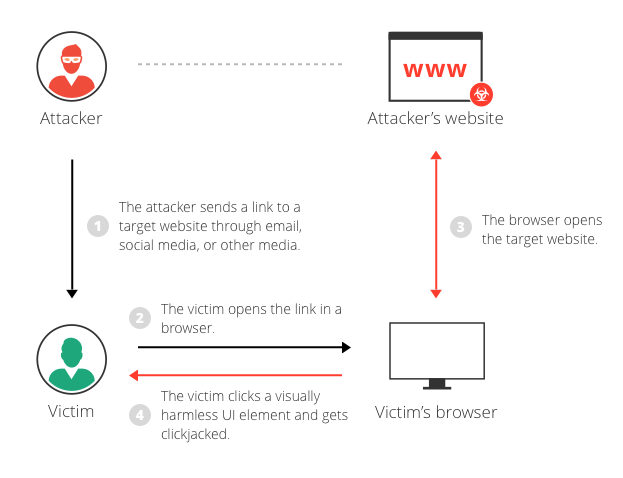
An iframe is also known as the inline frame. Clickjacking is for clicks not for keyboard. An iframe tag is defined using tags.
Experts examined it and concluded that if anything its a unique piece of malware in addition to it being a credible risk to LAMPP deployments. The attacker incorporates the target website as an iframe layer overlaid on the decoy website. It is a property which returns the window object of the iframe.
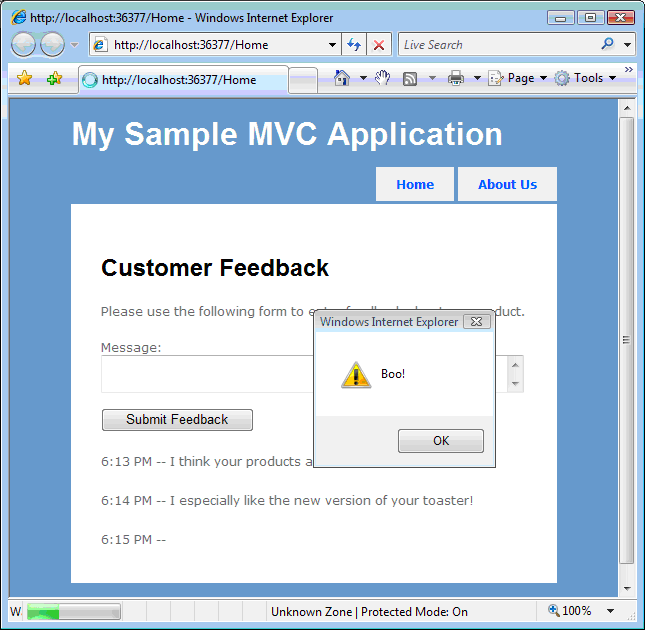
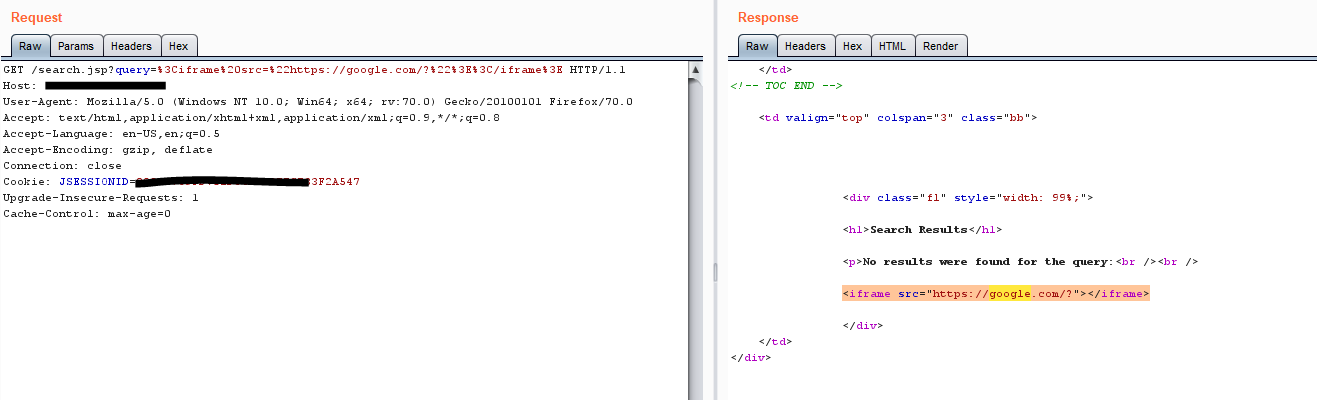
During this process unsanitized or unvalidated inputs user-entered data are used to change outputs. I got an email from Google saying that they added one of my sites to their list of bad ware sites the email was as follows. An example using the style tag and parameters is as follows.
What is clickjacking. There was a surge of iFrame code injection on some legitimate websites such as ABC news in 2008. The src attribute is used to specify the URL of the document that occupies the inline frame.
An HTML tag label pieces of content such as heading paragraph form and so on. Clickjacking is an attack that tricks a user into clicking a webpage element which is invisible or disguised as another element. You have to move in the directory in order to run the tool.
Attackers take advantage of the fact that the content of a web page is often related to a previous interaction with users. I am using an and trying to call one more iframe inside the main iframe but inside the iframe is not rendereing please help how I. Send the message from the parent element.
Security researchers from Armorize have intercepted a currently live mass iFrame injection attack affecting over. A Web application firewall can greatly help reduce the risk of. To run this example replace remotehost below with the address of the remote server on which the report engine is.
It returns the HTML content of. Track iFrame Conversions. Attacker crafts malicious link including his injected HTML content and sends it to a user via email.
Some of the definitions are given below. All we need to attack is to position the on the evil page in such a way that the button is right over the link. Cross-site scripting often abbreviated as XSS is a type of attack in which malicious scripts are injected into websites and web applications for the purpose of running on the end users device.
It is a tag used in HTML5 to embed an HTML document within a parent HTML document. Windowonmessage functionevent if eventdata message consoleMessage. An inline frame is used to embed another document within the current HTML document.
Use the following command to install the tool in your Kali Linux operating system. From the parent to the iframe. Nevertheless you need to pay attention when adding an iFrame from an untrusted site website.
90000 pages compromised in mass iFrame injection attack. The attack usually includes half a dozen drive-by exploits and also uses social engineering to get users to install something else such as a video codec that is actually a Trojan. The first step in recovering a website after an Iframe Injection attack is to shut it down completely during the cleansing process.
Linux Rootkit Found Launching iFrame Injection Attacks. Sarthy claims iframe injection attacks can be easily detected and fixed with online tools. Hypertext Markup Language HTML injection is a technique used to take advantage of non-validated input to modify a web page presented by a web application to its users.
Click Store and then View exploit. It returns the document object of iframe window. Clickjacking attacks use CSS to create and manipulate layers.
Set the opacity value opacity to ensure that the target iframe is transparent. This can cause users to unwittingly download malware visit malicious web pages provide credentials or sensitive information transfer money or purchase products online. It is used to get the object reference of an iframe.
When applications fail to validate user data an attacker can. As a further example the HTML markup below generates a simple web page with two divs the top div containing a heading and some text and the bottom div containing an IFrame with embedded report. The attack only affects mouse actions or similar like taps on mobile.
Thats usually doable with CSS. What is the difference between frame and iframe in Selenium. Now use the following command to move into the directory of the tool.
So that when a user clicks the link they actually click the button. Attacker discovers injection vulnerability and decides to use an HTML injection attack. Hi I need help understanding the iframe injection attack and how it is performed by the hacker and furthermore how it affects different accounts on my VPS - The reason I need to know is below.
Const myiframe documentgetElementByIdmyIframe myIframecontentWindowpostMessagemessage. Last week someone posted a module to the Full Disclosure mailing list which turned out to be a rootkit for Linux.

Frame Injection Attacks Netsparker
What Is Clickjacking Attack Example X Frame Options Pros Cons Imperva

Preventing Javascript Injection Attacks C Microsoft Docs

Https Sql Injection Blogspot Co Uk Iframe Injection

What Is Cross Site Scripting And How Can You Fix It

What Is Clickjacking Tutorial Examples Web Security Academy

The Difference Between Cross Frame And Cross Site Scripting Daniel Miessler
When I Found Iframe Injection And Illegal Redirect Dom Based By Mrunal Infosec Write Ups
0 comments
Post a Comment